Cyber-Attack: The Incident Response Team

Blind panic may be the first response to a cyber-attack, but family businesses and family offices need not fear if they follow training and a steady response. Three cyber experts at Schillings tell Daniel Bardsley how to react
Few things are worse for an organisation than falling victim to a cyber-attack, not least because the consequences can go well beyond the direct effects of having data leaked or made inaccessible.
The reputational damage can prove fatal.
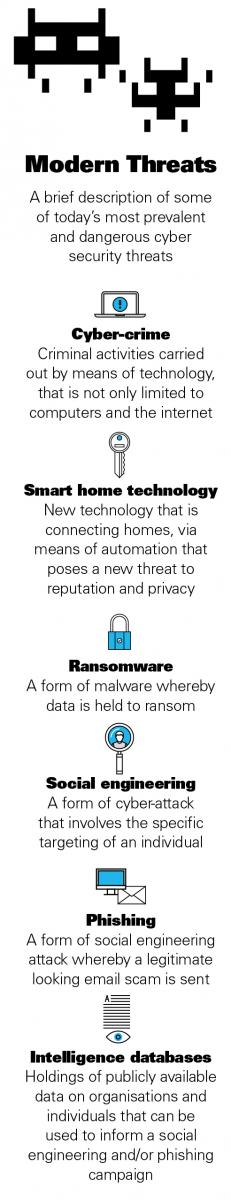
Yet despite the significance of a data breach—whether a ransomware demand, a phishing attack, a malware incident or anything else—companies and offices often have little idea how to respond. Blind panic is frequently the order of the day.
As Johannes Stillig, head of cyber at the reputation and privacy crisis law firm Schillings, puts it, staff often “run around like headless chickens because they are not prepared”. However, he assures that knowing how to react is not too complicated.
 “It starts with a list of people: Who are you going to call externally and internally? Who are you going to bring in to help you regain the situation?” Stillig says.
“It starts with a list of people: Who are you going to call externally and internally? Who are you going to bring in to help you regain the situation?” Stillig says.
The aim is to shut the attack down as fast as possible, preventing further information from being lost, while working out how extensive the breach has been and protecting vital evidence. This may require the involvement of multiple specialists, from digital forensics experts to ethical hackers—it is much more than the job of the regular IT staff. Legal efforts may focus on securing interim injunctions to prevent the publication of information.
“The IT team should play an important role, but should definitely be overseen by an external partner,” says Stillig.
Schillings produced with Campden Research Private and Confidential: The Cyber Security Report, which surveyed 121 individuals, most from single family offices and family businesses. Just over a quarter had experienced a cyber-attack.
As the only business in the world to bring together integrated teams of lawyers, cyber security analysts, intelligence specialists, investigators, and risk consultants, Schillings helps clients to deal with a myriad of reputational and privacy threats, of which cyber-attacks and data loss are just one example.
 “Our team matches up perfectly with the team at the host organisation that has suffered the breach. Part of our job is to departmentalise the responsibility and take the emotion out of it,” says David Imison, a Schillings partner.
“Our team matches up perfectly with the team at the host organisation that has suffered the breach. Part of our job is to departmentalise the responsibility and take the emotion out of it,” says David Imison, a Schillings partner.
Response plans should not be overly prescriptive, with the real value coming from getting individuals ready and rehearsing so that they know how to respond.
Also, says Magnus Boyd, another Schillings partner, these response plans will vary from organisation to organisation.
“There are fixed things that need to be reported, but while in one organisation it might be appropriate for the in-house lawyer or general counsel to coordinate the response, somewhere else it might be the communications person,” he says.
“We go into an organisation and look at various factors … What is important is that the incident-response plan is bespoke.”

One issue cyber-attack victims may face is how to respond to a ransomware attack.
If the data is worth more than the ransom, paying up may be the better option, although there are important caveats to this.

If handled incorrectly, a payment may lead to a demand for more money, or the individual demanding payment may not have the decryption tools to allow the victim to regain access to their information.
The process of trying to decrypt data can provide useful intelligence. It may indicate whether the cyber criminals have a serious, sophisticated operation or are less experienced. This, in turn, may determine whether it is worth paying a ransom.
While conceding it may seem a harsh statement to make, Stillig points out that an organisation that has to consider paying a ransom demand “has done everything wrong”. It should never have let itself get into this position.
“All you need to mitigate a ransomware attack is to have a decent back up of your data,” he says.
The cost of dealing with a data breach is always likely to be greater than the cost of putting in place measures to prevent such a breach, he says.
When the real cost of a data breach is factored in—like clients whose data has been leaked not returning—the difference is even more stark.
“It may be a very small data breach, but as soon as you inform your clients, they may decide to take their business elsewhere, for good,” says Stillig.
“It is not so much about the immediate investment in new hardware—that is peanuts. It is what happens afterwards.”
As Boyd puts it, for most single family or multi family offices, a loss of data “will be an existential threat”.
“You have got to appreciate the value of information and the consequences if it is lost,” he says.
Family offices often focus on service rather than security, so they frequently make data freely available to all staff. Restricting access to only those who need it is a better option, as these individuals can be given additional security training.
There are many other precautions organisations should take.
A “bad leaver” situation, in which a disgruntled former staff member leaks or threatens to leak data, can be prevented by improved pre-hiring vetting procedures, tighter contractual arrangements when individuals enter or leave, and the removal of access to the organisation’s systems on exit.
“The cost has been huge to families where they have seen someone run off with their data and it has ended up with a dispute,” says Imison.
If all such precautions fail, there is only one option if a data leak happens: Let clients know immediately. The worst thing, notes Imison, is if they find out from a third party, such as the media, or are told there was no problem, only to find out later there is one.
However, a small family office might, quite sensibly, want to deal with a data breach without encouraging outside interest.
“You can have all the controls—technical controls, process controls—to protect your information or organisation, but all it takes is one wrong click by an employee or family member, and all of those controls are immediately circumvented,” Stillig says.
And what about unmasking the perpetrators? By combining their forensic investigations and intelligence capabilities, and by putting their lawyers to work alongside local law enforcement, Schillings has had success in putting cyber criminals in prison.
“It is our speed of response that enables us to get from problem to solution in the shortest possible time,” says Boyd.
“Ultimately, how you respond in the first 24 hours to a cyber-attack can make all the difference.”
Interested in receiving the report? Find out more at campdenresearch.com